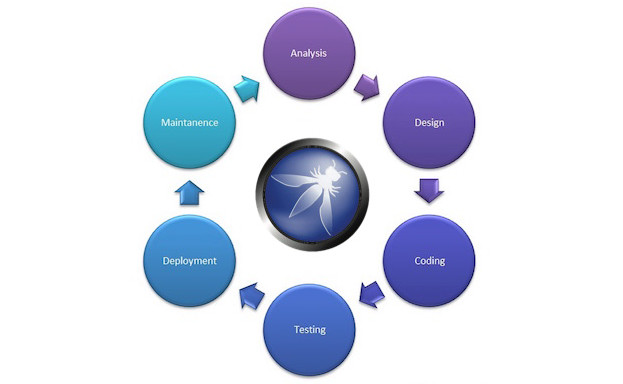
Majority of strategic business processes are supported by applications, yet application security continue to receive less budget & attention than network security.
High profile data breaches have resulted in awareness of the repercussions of a cyber-attack. Businesses realize hackers are attacking applications and according to various surveys, security leaders agreed there is need to improve the application security programs to lower the risk of a breach.


 ,
,