The value of your company is its data
As such you need a security program that provides a framework for keeping your company at a desired security level by assessing the risks you face, deciding how you will mitigate them, and planning for how you keep the program and your security practices up to date
Security is not merely tools, but a process. It’s more than designing and deploying tools and controls into a system; it involves designing an end – to – end secure system such that, all security measures, including processes and procedures work together.
Why hire Aimdeep for your Infrastructure Security Solutions?
Most organizations, when implementing Infrastructure Security solutions are overwhelmed by many processes, integrations, and policy-enforcement challenges once the system is rolled out.
Aimdeep has industry-proven easy to implement plan that is designed and streamlined to save your team time on solutions, vendor evaluation and the challenges of simulating deferent scenarios.
IT Infrastructure Security-Step by Step
- Comprehend your IT infrastructure, network configuration and topology, network traffic and communication system
- Prepare a security policy, processes, procedures, and their implementation plans
- Obtain approval from senior management
- Implement the policies and plans
- Maintain thorough documentation of the entire IT infrastructure
- Periodically test and audit the entire network, update it regularly, and maintain an audit trail of all changes
- Create security awareness among users through training, crash courses or “tip of the day” messages.
- Be proactive to minimize mitigation measures
Security Model for Implementing a Defense-in-Depth Security Solution
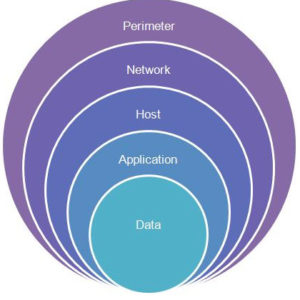
Layer – 1 : Perimeter Defense
Layer – 2 : Network, Servers, and OS
Layer – 3 : Host Protection
Layer – 4 : Application Protection
Layer – 5 : Data Protection
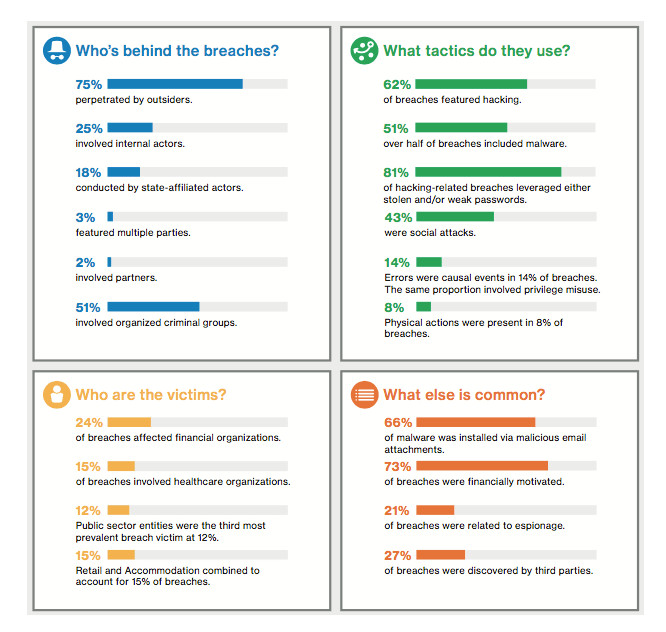
According to Verizon Data Breach Investigation Report
75% of attacks are from external while 25% are from internal vices. These statistics clearly indicates where most of the effort of securing the IT Infrastructure should be directed to. This paradigm shift, presents major challenges to organizations whose environment were setup for the reverse ratios.
With proliferation of cloud and mobile computing, most organizations have multiple applications across multiple networks spread over wide geographical locations. It is the responsibility of the organizations to verify that the technologies used to setup the IT Infrastructure and processes are as secure as the vendors claim.
Having a security program should mean that you’ve taken steps to mitigate the risk of losing data in any one of a variety of ways, and have defined a life cycle for managing the security of information and technology within your organization.
You don’t have to experience a business loss resulting from a security incident. If you have a security program and you do experience a loss that has legal consequences, your written program can be used as evidence that you were diligent in protecting your data and following industry best practices.
The important thing is that you have a security program and that you use it to address your company’s security in an organized, comprehensive, and holistic way.
Aimdeep will help you to
- streamline your security program and let you focus on your core business processes
- identify and stay in compliance with the regulations that affect how you manage your data.
- deploy an IT Infrastructure life cycle process that ensures your security is continuously adapting to your organization and the ever-changing IT environment.
- keep in good relationship with your customers so that you can meet both your legal and contractual obligations.
Virtualization Security : Dynamic IT Environments Demand Adoptive Security
Today’s IT organizations must secure interactions between users, applications and data, in an environment that is changing and becoming increasingly dynamic—from public and private multi-cloud environments to the proliferation of mobile devices.
As the Cloud services become more and more elastic, so should the security methods used to secure the organization’s services hosted on the Cloud.
Organizations are finding themselves having to do much with less budget and operations personnel. Having a single point of managing organization’s security ensure consistency, easy of use, and faster response to security incidents.
Secure Mobile Infrastructure
As the proliferation of mobile devices permeates the IT the industry, the need for organizations to design a secure mobile infrastructure to support them continues to grow. Secure Mobile Infrastructure planning provides both employees and customers the connectivity and functionality needed while ensuring companies maintain control of the mobile security and support.
Employees, customers and vendors are using smart phones, tablets, wearable gadgets, and laptops more and more to connect to your company’s resources.

Aimdeep will help give experience and expertise to your support teams to help architect and implement the best in mobile security environments.
The Challenges of Mobile access
There are many hurdles of complexity, associated with laying down the support systems required to manage mobile devices. The biggest will be identifying what’s a business versus personal device on your network.
While business assets that stay at the organization’s location are more manageable, when they leave the confines of your organization’s location, they can be a danger to the organization because they are carrying, or granting access to, company digital data information that a cyber criminal would like to get their hands on.
Challenges Include
| Bring-Your-Own-Device issues | Device loss or theft | Company data leaving the office |
| Viruses, Spyware, and Malware | Email data issues | Password policy complexities |
| Device lock-down best practices | Device Tracking | Software administration |
| Operating System update holes | VPN connectivity | Carrier compatibilities |
| Application distribution | Data Loss Prevention (DLP) strategies | Privacy concerns |
Mobile Device Management (MDM)
Having a reliable MDM is important to help laying a good foundation to maintain mobile security needs; however, it’s only one part of the equation.
MDM client software installed on the device allows your operation administrators to track assets, manage encryption, control email access, and remotely manage all the security options on the mobile device, as needed.
There are several vendors on the market that provide MDM toolkits and instructional advice. However, it’s up to your teams to architect and address your unique business protection and prevention needs, which directly impact your employee and customer mobile devices accessing your network.
Aimdeep provides the industry experience to help assess your environment’s needs, identify and deliver security implementation strategies, and work with your teams to implement a fully architected, safe, and solid solution.
Our mobile security experts can assess your Endpoint permission needs and create a plan for a secure workflow to help mobile device users get the most benefits from your security technologies.
At Aimdeep we also help build secure industrial automation and control system (IACS) network infrastructures to integrate Internet Technology with Operational Technology such as SCADA systems
As the world of connectivity dramatically integrates 30 billion objects by 2020, so do the challenges to secure these “inextricable mixture of hardware, software, data and service” grow exponentially
Aimdeep brings the expertise of building large scalable systems to cope with demands from IoT objects

 ,
,